
5G and the cyber security challenge
Posted on 25th June 2019 by Phil Ainley
On Thursday 30th of May 2019, 5G connectivity from EE went live here in Manchester.
Manchester is among the first 6 major UK cities to have been chosen by the mobile network to benefit from the first phase of their 5G launch in 2019.
The other cities to benefit from the initial 5G roll-out in the UK are London, Birmingham, Cardiff, Edinburgh and Belfast.
What’s the difference between 5G and 4G?
5G comes with the promise of faster speeds, for both data downloads and uploads, and broader and more reliable connectivity.
Exactly how fast the speeds will be remains to be seen, but this fifth generation of mobile connectivity will undoubtedly put its predecessor to shame.
Speeds will vary depending on factors such as where you are located, what network you are connecting to, how busy that network is, and what device you’re using.
Digital Trends has said that some download speeds are expected to reach 10Gbps yet could be as slow as 1Gbps. An average speed could be upwards of 50Mbps. The time it takes to send data could be as quick as 1 millisecond in some cases, with the speed being nearer 10 milliseconds in general. All-in-all the whole network will be significantly quicker than anything before it.
However, to experience the initial benefits of 5G you will need to buy a new mobile phone.
Supporting the development of 5G
As with most, if not all, technological advancements there comes a new and previously uncharted level of risk for many industry verticals in 5G use cases.
The National Infrastructure Commission (NIC) states in its Connected Future report, that “Securing the mobile networks necessary to put the UK at the forefront of this emerging technology will be critical to the growth of our economy.”
As such, it is vital that UK research and development understands and meets the security challenges that 5G poses. UK Government allocated £10 million of funding in the 2017 Autumn Budget (Section 5.19 Digital Communications) for this so 5G networks could be tested, working with the National Cyber Security Centre.
Industry verticals in 5G use cases as identified in the 5G Architecture and Security report
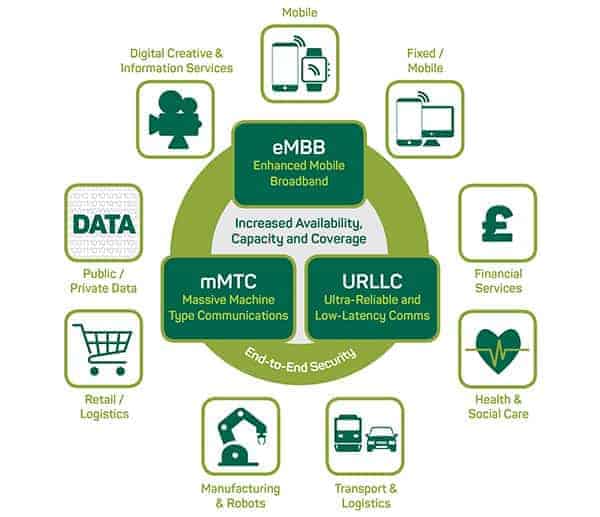
Identifying the business reasons for 5G security
5G poses a complex and diverse range of reasons for enhanced security along with a broad set of stakeholders who will benefit from 5G security measures, these include:
- Network operators – At the core of the 5G revolution, the networks need to protect their revenue and their brand reputation, which include protecting consumer data from breaches. They also need to meet both license and compliance conditions, such a Data Protection.
- National concerns – These include infrastructure and the economy, the emergency services networks, law enforcement, utilities such as water and power, and support for global trade communications.
- Over-The-Top (OTT) App providers – Over the top refers to content providers that distribute streaming media as a standalone product directly to viewers over the Internet. OTT bypasses telecoms, multichannel television, and broadcast television platforms that traditionally act as a controller or distributor of this content. 5G will help to significantly improve the quality and reliability of streaming services which will enhance the user experience.
- Businesses and Individuals – For online gamers, 5G could be a ‘game changer’ and those of us who can’t live without our mobile phones should enjoy a much slicker and quicker online experience. Ideal if you’re a vlogger or influencer through social media.
For businesses it could open a whole world of innovation opportunities including the chance to improve efficiencies and output via automated machinery.
However, it’s important to remember the increasing amount of diverse industry verticals that 5G will support and the challenges that comes with that.
What are the security challenges of 5G?
5G networks support a lot of connected devices at once, thus creating cyber security challenges that stem from the attributes that make 5G such a great technological advancement.
One of the key concerns is the Internet of Things (IoT). Since 5G enables IoT to be much larger than before, this generates and increased risk of cyber-attack. The vision for IoT is for millions of devices to be connected with the internet and each other. This will allow people to communicate with machines and enable machines to communicate with other machines.
The age of 5G will enable the creation of a vast array of new services. Each of these services will need varying levels of security.
Some IoT examples that will benefit from 5G and possibly become reliant on it include; driverless cars and other automated vehicles such as drones and warehouse robots. The healthcare industry will benefit from remote patient monitoring and remote surgery and the ability to transfer large amounts of patient data in one go.
Failures in both of these areas could lead to serious accidents and/or the theft of personal medical data. This will result in both of these areas of demanding increased cyber security and stronger methods of authentication, such as biometric identification such as fingerprint door access and/or facial recognition software.
If we want to look closer to home to highlight the potential cyber issues of 5G, your Smart Home will be heavily reliant on the improved technology. How would you cope if your home was hacked?
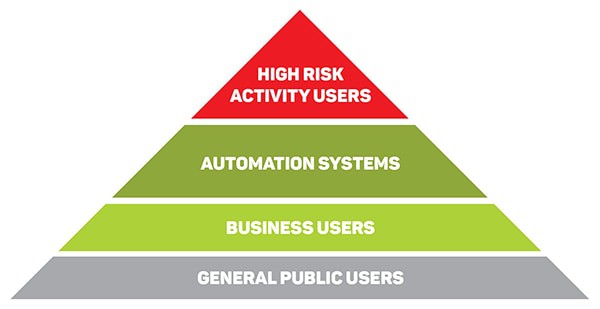
The threat to Risk Owners
It is widely thought that a completely secure network will never be possible. No matter how sophisticated a network is, there will always be someone who is skillful enough to break into it.
It is essential to address the issues that affect those people or organisations who have the greatest amount to lose. This could be an unavailable system, a system that loses integrity or a system that is no longer confidential. These users are known as the ‘risk Owners’ in the security industry.
The Risk Owner pyramid diagram highlights a higher risk per user at the top of the pyramid. As the pyramid widens the risk per user is thought to lessen, yet the number of users at risk increases.
Tackling the 5G security challenge
The Department for Digital, Culture, Media and Sport released a detailed 5G Network Architecture and Security report in December 2018. The report identified 5 security layers in a 5G system while also outlining four security measures that 5G needs to meet.
| 5 security layers in a 5G system | |
| 1. | Services, Applications and Use Cases |
| 2. | Users, Things and Equipment |
| 3. | Inter-networking |
| 4. | 5G Mobile Network and Virtualisation Systems |
| 5. | Physical Infrastructure |
4 security measures 5G needs to meet
- Cross-layer security. A unified framework to coordinate different security methods for each security layer.
- End-to-end security. Secure connection for the communication paths between the user and the core network.
- Cross-domain security. 5G networks create a use cases with unique requirements. The report calls for cooperation between those in the 5G system to enact integrated security solutions across domains.
- Secure-by-design. As the network changes and evolves, security must be built into the design during development.
To ensure a strong and healthy 5G communications network businesses need to maintain their focus on enhanced cyber security and could benefit from comprehensive cyber insurance.
Caunce O’Hara is a business insurance broker offering protection to freelancers, contractors and small businesses. Insurance is vital to all businesses, especially to start-ups. If you would like a competitive online quotation for your business insurance, please click the green button, it only take a few minutes.
Click here for a quick online business insurance quote
Related Articles:
Cyber stalks businesses of all sizes
Reducing your cyber risks on the railways
Tips for Protecting Your Small Business From Cybercrime
Credits:
Information has been derived from the following sources:
- Institute for Communication Systems – 5G Whitepaper
- National Infrastructure Commission – Connected Future
- UK – 2017 Autumn Budget
